Today while browsing a (compromised) WordPress site that shall remain unnamed, I came across a very interesting “hack” that was pulled off with a bit more finesse than most of the drive-by-infection attempts. This one relies on using JavaScript to change the text rendering, causing it to resemble mis-encoded text with symbols and rubbish in place of the content, then prompts the user to update “Chrome’s language pack” to fix the problem.
Here’s a screenshot of the initial step of the ploy:
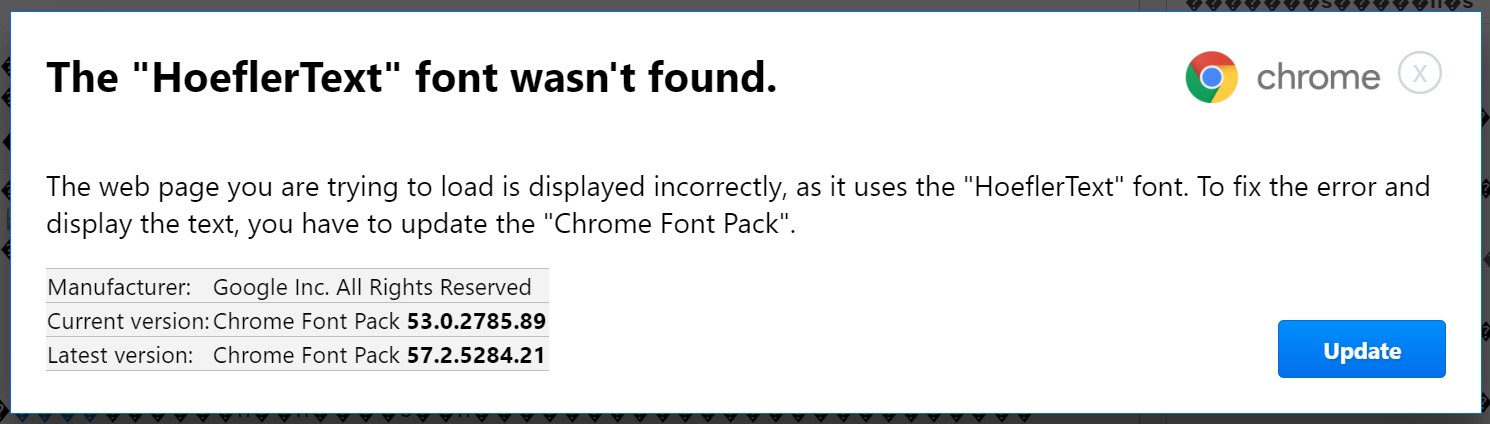
And here’s the prompt up close:
This attack gets a lot of things right that many others fail at. The premise is actually believable: the text doesn’t render, and it says that is caused by a missing font (HoeflerText, which is a real font, by the way!), which it then prompts you to download and install.
The usage of a a clean, well-formatted dialog to present the message with the correct Chrome logo – and, more importantly, – the correct shade of blue for the update button. The shape of the update button seems correct, and the spelling and grammar are definitely good enough to get a pass.
At the same time, there are some tell-tale signs for the paranoid careful.1 My browser string is easily accessible via window.navigator.userAgent and exposes the correct version of Chrome (Chrome/56.0.2924.87), but the dialog has version 53 hard-coded in there. Personally, I’d also have omitted the Ⓧ in the corner, as that’s the only part that seems out of place in the prompt.
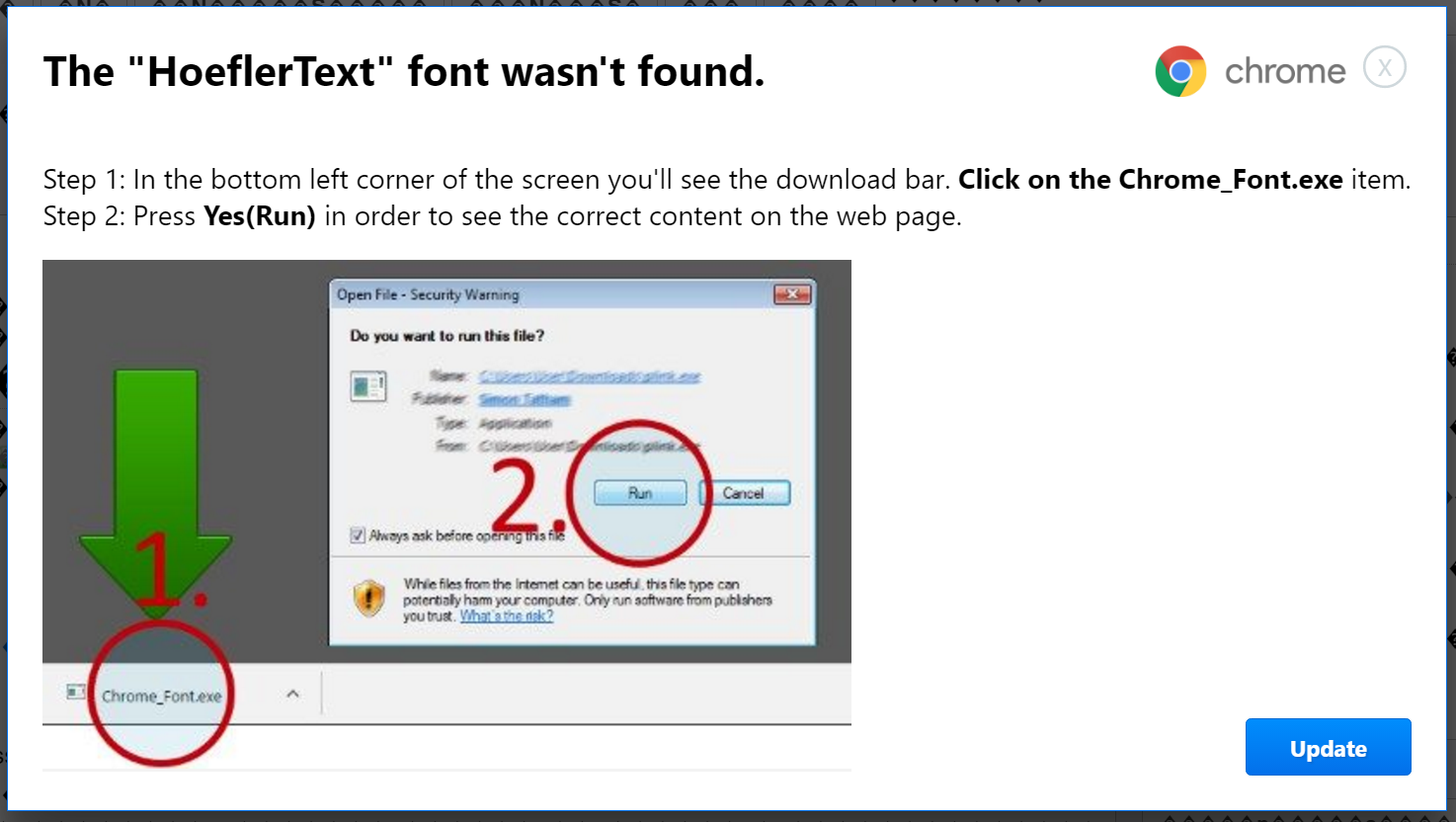
Clicking ‘Update’ (merely out of curiosity!) results in a file “Chrome Font v7.5.1.exe” to be downloaded, and the webpage morphs to “helpfully” encourage the user to run the virus:
At this point, the quality of the social engineering attack takes a nosedive, as do its chances of success. While Chrome does not catch the download as being malicious,2 it is however blocked by the “this file isn’t downloaded very often” warning (which I personally – speaking as someone lucky enough not to be affected by this – despise as it does impose a rather hefty and unfair bar on independent software developers).
The image in the popup dialog contains several discrepancies, but first, here it is blown up:
The blurring in the dialog is not from me – that’s how it was presented. It shows a UAC prompt to run a signed executable, which the download most certainly is not. The name of the file in the “help image” is Chrome_Font.exe, while the downloaded file is called “Chrome Font v7.5.1.exe” (which doesn’t match the so-called “new version” from the first popup dialog, but that’s easily forgivable). It does not reflect the “not often downloaded” error that is seen, which makes it highly unlikely that the file can be accessed. Also, the download does not have a file icon, whereas giving it the Chrome icon would have been trivial.
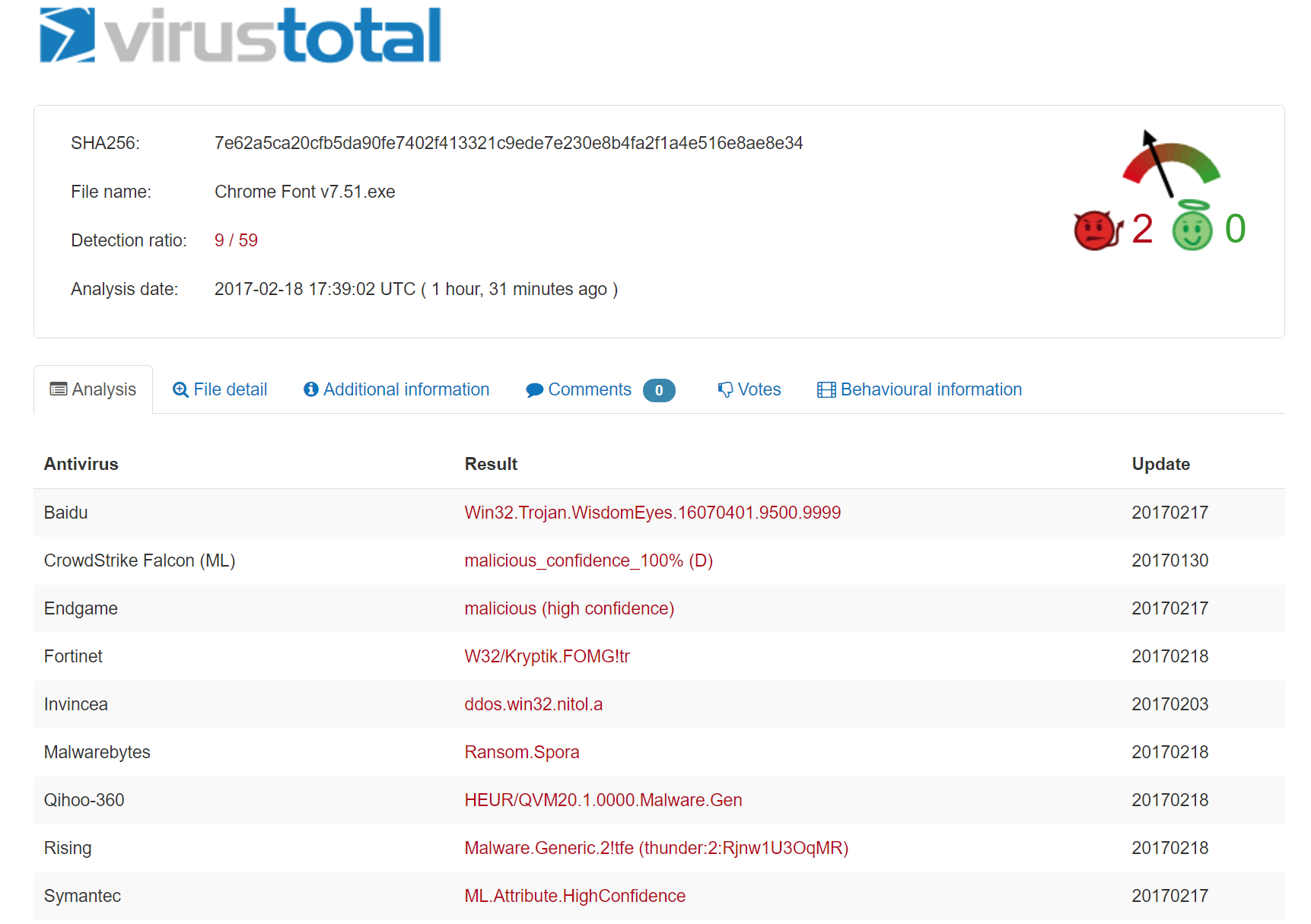
All that aside, the file in question is not caught by Windows Defender or Chrome as being malicious. An upload to VirusTotal reveals it as never-before-seen, with only 9 out of the 59 antivirus scanners in its database correctly identifying the file as malware, and most only via heuristics at that:
Now you know. Be careful and safe browsing!

https://blog.brillantit.com/exposing-eitest-campaign/
A .exe file? Are you sure this is a Chrome hack? because this shit is not gonna work on Linux lol
Wow, Carl! Linux! You are so cool!
Quick, you have less than 4 seconds to find the fanboy in the room! What do you do?
Very good, sarcasm to the rescue. Now you can feel superior despite your shittier OS. Isn’t life good now?
Got WINE installed Carl? You would be surprised what a Windows malware .EXE can do in Linux…
As a Linux user myself, I set a Windows on Chrome User-agent just so I get to see more of these kind of malwares.
Fanboyism aside, he’s right. This is not so much a “Chrome hack” as it is a phishing attack targetted at Chrome users prompting them to install Windows malware which will indeed not work on other operating systems.
No need to bash anyone here.
On-topic: I agree that the X button looks out of place, but maybe it would’ve been more believable had they used a notification bar at the top of the page, as this is what Chrome tends to do in the case of missing plugins etc.
This is definitely an attack targeting Chrome’s Windows users exclusively, not even WINE users on Linux would be susceptible to this one. But OS X is also immune. Honestly, it just makes no sense to develop a similar attack for Linux given its minuscule share of the market and the generally more tech-savvy nature of its users, but don’t be surprised if we see a lot more OS X ransomware in the future.
The only mitigating factor there is that Apple has recently disabled by default the running of non-signed executables entirely – a bold move that I personally dislike but can admit makes the most sense in the grand scheme of things.
Interestingly enough, Microsoft actually developed the framework to do the same long, long before Apple and there are group policy options to disable the running of non-authenticode’d binaries, but the world would go mad if Microsoft enabled that by default, but I have consulted for a few organizations that had that enabled sitewide (via Active Directory) to great effect.
@Mahmoud Al-Qudsi
This is incorrect, it does not only target Chrome’s Windows users… It is an exploit kit. It also targets Internet Explorer users. You can try to visit the same website using IE and you will have another malicious code injected.
Thank you
@reader: no, the attack in particular that is described in this article as depicted targets Chrome users. Even if the people behind it are targeting multiple browsers with different-looking attacks. I do not doubt that there are other components in the grand scheme of this exploit kit that target users of other browsers as well, but that has no bearing on the discussion taking place here in the comments. Your pedanticism is noted, however; and (no sarcasm implied) the additional information is appreciated as well, even though it does not disprove the particular point being made.
Does anyone know what the malware does and what type of malware it is, i.e., virus, trojan horse, etc.?
After years with WordPress and taking the usual security precautions, I was surprised to visit my site recently and find this very exploit. After logging in and changing the password, I checked and WordPress didn’t have a log-in by anyone but me, and WordFence had nothing to indicate any other IP had succeeded in getting inside. But the code that brought up the spoof screen was definitely in the HTML. Is it reasonably possible that someone else’s site with that host was compromised and the spoof spread that way?
My site is infected. Many users complained. My site runs on older version of Wordpress. Is this at the file level or database level. Is there a specific set of files I can recover.
The binary will not be named “Chrome Font v7.5.1.exe” for another user. The version, which is here 7.5.1 is generated base on your IP address. Also, it is irrelevant to say that the malware is detected at 9/59, because they are changing it every hour or so. See https://blog.brillantit.com/exposing-eitest-campaign/ for a detailed analysis of the threat.
@Al: the brilliantit post that has been spammed repeatedly here in the comments does cover that. It’s a great article and the team there did a good job dissecting this. The payload can differ, the delivery method is what is consistent here, but depending on what the attacker wants the payload could be to join your PC to a botnet, ransomware, or something else entirely.
@Samir: the honest advice is that a compromised server is a compromised server and aside from wiping everything and restoring a clean backup (and by everything I mean from the OS up), there’s no way of guaranteeing that you’re not (still) compromised.
Now practically speaking, not an approach that I can officially condone, but this particular WP exploit modifies WP’s installation files. If you uninstall all plugins and themes, then nuke your WP install (including your
wp-config.phpfile), then re-install a clean copy of the latest WordPress version and connect it to your old database, that should definitely be a good start.@John Moore: if you don’t control the hosting environment, anything is possible. It depends on your host and how they have it configured, if they really don’t have privilege separation between different users – that’s insane.
Please note that this exploit (like most other WP exploits) doesn’t involve getting your login password and the attacker does not log in to your admin account or any other. They bypass the WP auth mechanism entirely and just use the vulnerable attack vector to install the payload. So all in all, it probably didn’t come from another user on the VPS but more likely via a vulnerable plugin or theme you have installed (or even if it took you 5 minutes to upgrade to the latest WP release).
My computer was targeted this morning. I was not thinking in the slightest and just clicked update font as it popped up on a very normal and frequently visited site…then it downloaded the malware, this was exactly @ 9:29AM.
Then at 12:09PM, about 3 hours later, I went to upload a document from a “folder” I had on my desktop, and noticed every folder I had ever made had disappeared off my desktop . Please note every other standalone file was still sitting on my desktop and not effected…just the folders and whatever was inside of them had disappeared.
I had tax documents, social security number, emails, addresses, all in that folder.***
I put a freeze on my credit and SSN, put a verbal password only I would know on all my bank accounts, and changed primarily every password I could think of that would be saved on my computer….and got a new computer already..
I know they have a lot of important info, so is there a very high chance they try to use my info? As of now I have followed every protocol for someone who’s identity may be compromised, so I should be fine, I was just wondering what could happen down the line?
I wonder if adblocker block this window??
I am a ordinary users from China, unfortunately, has experienced a terrible events described above. Who can tell me, what should I do?