Twitter has a new-ish feature that lets you embed only the video from another post or tweet in a post/tweet of your own (without quote-replying the source tweet itself). Only the video is then embedded in your post, and a small attribution appears at the bottom identifying where the video came from:
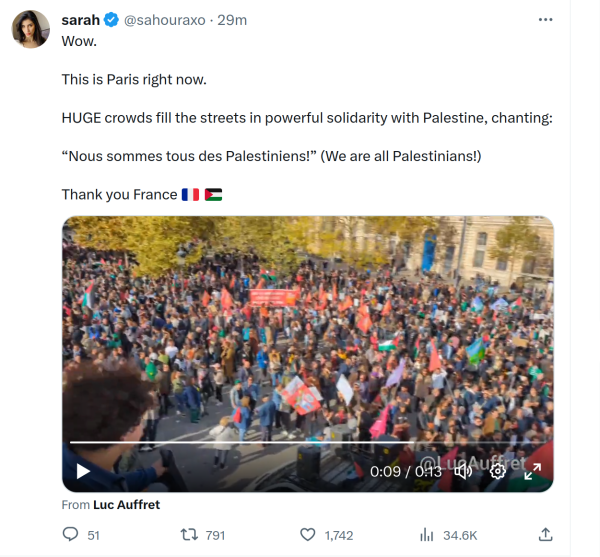
In the screenshot above, Sarah is sharing a video that was originally shared by Luc, but she’s not embedding/quoting Luc’s tweet itself – only the video. This post will cover how to do that yourself, both on the desktop/web and in the iOS Twitter app on iPhone.


 This post is for the C# developers out there and takes a look at the interesting conjunction of
This post is for the C# developers out there and takes a look at the interesting conjunction of  A few days ago, we published a new version of both the
A few days ago, we published a new version of both the  Hot on the heels of
Hot on the heels of 
 Windows 11 is here and it comes with a new version of Segoe UI Emoji, the font that’s used across the OS to render various emoji from Unicode codepoint sequences to the emoji you see on screen (developers:
Windows 11 is here and it comes with a new version of Segoe UI Emoji, the font that’s used across the OS to render various emoji from Unicode codepoint sequences to the emoji you see on screen (developers: