 This is a post that should probably have been made a little earlier, but we’ve been rather busy cranking out new EasyBCD versions and working on some exciting new developments. We’ve had a lot of questions regarding EasyBCD‘s compatibility with Windows 8, and what our findings are regarding the new Windows “touch-enabled” bootloader screen. In this post, we’ll cover the new bootloader and what works and doesn’t with EasyBCD.
This is a post that should probably have been made a little earlier, but we’ve been rather busy cranking out new EasyBCD versions and working on some exciting new developments. We’ve had a lot of questions regarding EasyBCD‘s compatibility with Windows 8, and what our findings are regarding the new Windows “touch-enabled” bootloader screen. In this post, we’ll cover the new bootloader and what works and doesn’t with EasyBCD.
The New Windows 8 Bootloader
Literally the very first thing you notice when installing and testing Windows 8 Developer Preview is the new boot screen. I personally find it to be very cluttered and unorganized, and generally aesthetically unappealing. However, compared to the decades of text-based boot selection menus that people are accustomed to, reviewers are seeing this as a dramatic improvement.

 Hello everyone! We have a new EasyBCD build with relatively minor changes. In keeping with our promise to release more often, we’re releasing this small EasyBCD updated that brings brings exactly one update, one new feature, and one bugfix to the table.
Hello everyone! We have a new EasyBCD build with relatively minor changes. In keeping with our promise to release more often, we’re releasing this small EasyBCD updated that brings brings exactly one update, one new feature, and one bugfix to the table.
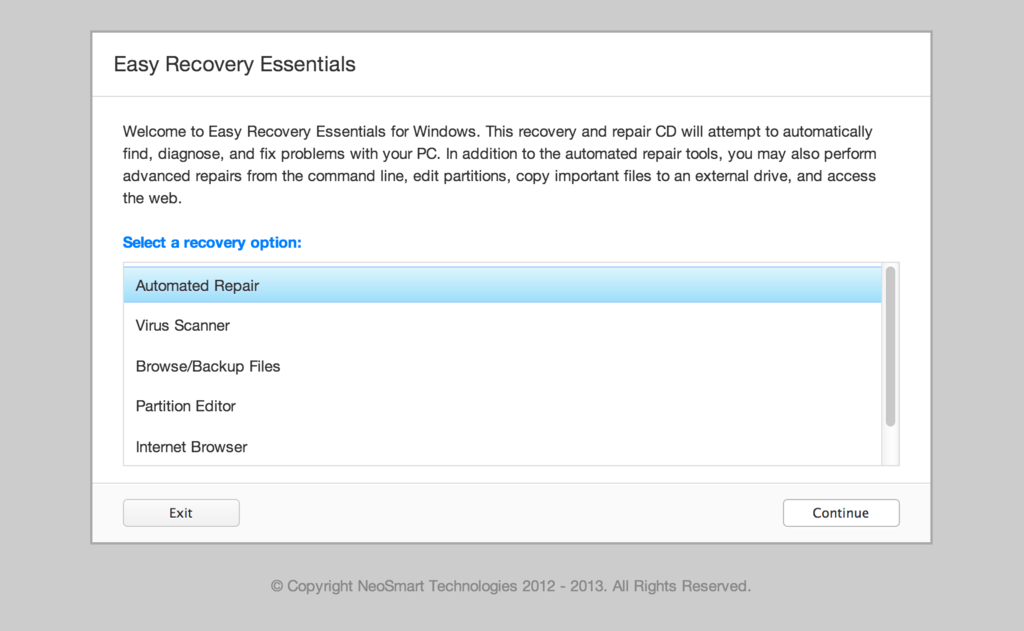
 Over the years, we’ve added more recovery CDs to the collection, ending up with a complete portfolio of repair CDs for Windows Vista and Windows 7 in both 32- and 64-bit flavors. We’ve had the good fortune of being able to host these CDs on our site in one form or the other for free download to millions of users around the globe.
Over the years, we’ve added more recovery CDs to the collection, ending up with a complete portfolio of repair CDs for Windows Vista and Windows 7 in both 32- and 64-bit flavors. We’ve had the good fortune of being able to host these CDs on our site in one form or the other for free download to millions of users around the globe.